Future-Proof Your Tech Stack
Future-Proof Your Tech Stack
Future-Proof Your Tech Stack
Without ripping out what already works. Modern architecture, practical approach.
Without ripping out what already works. Modern architecture, practical approach.
Without ripping out what already works. Modern architecture, practical approach.
Without ripping out what already works. Modern architecture, practical approach.
Milemarker™ works with your team, not around it.
Milemarker™ works with your team, not around it.
Milemarker™ works with your team, not around it.




Your Business Demands Data.
Your Architecture Demands Control.
The pressure from above
“We need real-time advisor dashboards.” “Can you connect Orion to Salesforce?” “The board wants profitability by office.”
Your reality
Point-to-point integrations that break. Vendor APIs that change without notice. Data silos that violate your governance standards.
The impossible choice
Give the business what they want and compromise your architecture. Or maintain your standards and get blamed for blocking growth.
There's a third option.

Your Business Demands Data.
Your Architecture Demands Control.
The pressure from above
“We need real-time advisor dashboards.” “Can you connect Orion to Salesforce?” “The board wants profitability by office.”
Your reality
Point-to-point integrations that break. Vendor APIs that change without notice. Data silos that violate your governance standards.
The impossible choice
Give the business what they want and compromise your architecture. Or maintain your standards and get blamed for blocking growth.
There's a third option.
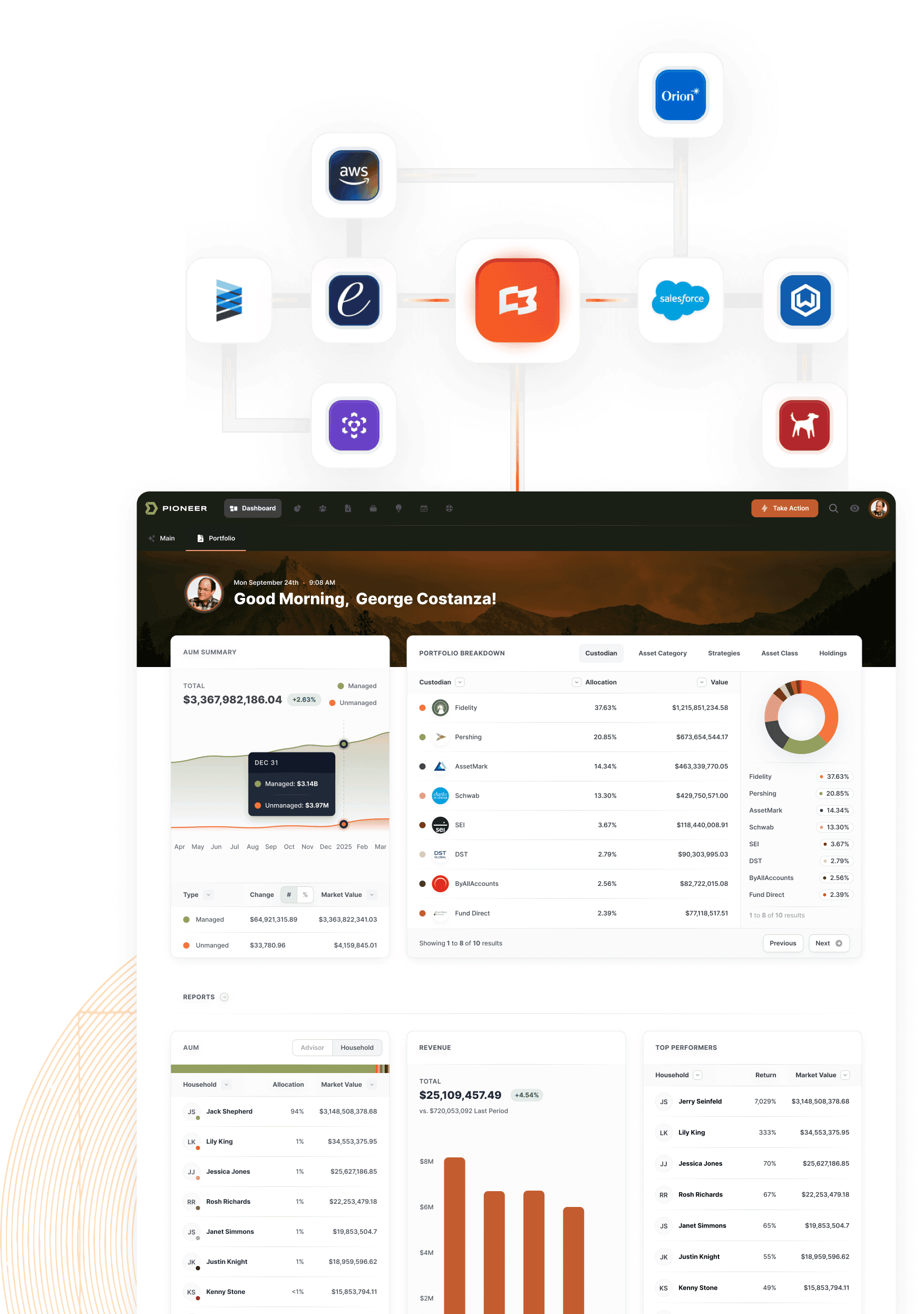
Enterprise Infrastructure
Enterprise Infrastructure
That Scales With Your Standards
That Scales With Your Standards

Centralized Data Architecture
Centralized Data Architecture
Snowflake-native data warehouse that consolidates all your wealth management data while maintaining your security, governance, and compliance requirements.
Snowflake-native data warehouse that consolidates all your wealth management data while maintaining your security, governance, and compliance requirements.

API-First Integration
API-First Integration
Connect to your existing systems through secure, standardized APIs. No more brittle point-to-point connections or vendor lock-in.
Connect to your existing systems through secure, standardized APIs. No more brittle point-to-point connections or vendor lock-in.

Your Security Standards
Your Security Standards
SOC 2 Type II compliance, encryption at rest and in transit, role-based access controls, and audit trails that meet your enterprise requirements.
SOC 2 Type II compliance, encryption at rest and in transit, role-based access controls, and audit trails that meet your enterprise requirements.

Technical Control
Technical Control
You own the data architecture. You control access policies. You define the integration standards. Milemarker provides the platform.
You own the data architecture. You control access policies. You define the integration standards. Milemarker provides the platform.
The Technical Reality
The Technical Reality
The Technical Reality
Integration Requests = Custom Development Projects
Data Governance = Hope Vendors Don't Change APIs
Security Compliance = Managing 12 Different Vendor Policies
Scaling Data = More Complexity, More Risk
Integration Requests = Custom Development Projects
Data Governance = Hope Vendors Don't Change APIs
Security Compliance = Managing 12 Different Vendor Policies
Scaling Data = More Complexity, More Risk
Integration Requests = Custom Development Projects
Data Governance = Hope Vendors Don't Change APIs
Security Compliance = Managing 12 Different Vendor Policies
Scaling Data = More Complexity, More Risk


Integration requests
configuration, not development

Data governance

centralized policies & standards

Security compliance

single SOC 2 platform

Scaling data

add capacity, maintain architecture
Real CTO Results
Thanks to Milemarker™, our leadership team and advisors now have greater access to the data we need to effectively run our business.

Laura Hubbell
Chief Information Officer at SignatureFD
Thanks to Milemarker™, our leadership team and advisors now have greater access to the data we need to effectively run our business.

Laura Hubbell
Chief Information Officer at SignatureFD
Thanks to Milemarker™, our leadership team and advisors now have greater access to the data we need to effectively run our business.

Laura Hubbell
Chief Information Officer at SignatureFD
Thanks to Milemarker™, our leadership team and advisors now have greater access to the data we need to effectively run our business.

Laura Hubbell
Chief Information Officer at SignatureFD

90%
reduction in custom integration development

90%
reduction in custom integration development

90%
reduction in custom integration development

90%
reduction in custom integration development

Centralized
security and compliance management

Centralized
security and compliance management

Centralized
security and compliance management

Centralized
security and compliance management

Unified data
governance across all systems

Unified data
governance across all systems

Unified data
governance across all systems

Unified Data
governance across all systems

Scalable
architecture that grows with the business

Scalable
architecture that grows with the business

Scalable
architecture that grows with the business

Scalable
architecture that grows with the business

Technical
Architecture




Snowflake-Native Platform

Columnar storage & elastic compute scaling

Zero-copy data sharing & time travel capabilities

Native BI tool connectivity (Power BI, Tableau, Sigma)

Enterprise-grade security & compliance
Infrastructure Compatibility

Works with your existing data lakes & warehouses

Native integration with Snowflake, Databricks, Azure & Google Cloud

Supports current SQL architecture & query patterns

Connects to existing data infrastructure without migration








Security & Compliance

AES-256 encryption at rest & in transit

Customer-managed encryption keys (CMEK) support

Role-based access control (RBAC) at table/column/row level

Complete audit logging & compliance reporting
Integration Framework

130+ pre-built connectors for wealth management platforms

Custom API development for proprietary systems

Real-time & batch data processing capabilities

Change data capture (CDC) for system synchronization





Built for
Enterprise CTOs


Your Standards, Your Control

Deploy within your cloud environment or use our managed service

Implement your data governance policies & access controls

Maintain your security standards & compliance requirements

Control data residency & retention policies


Your Standards, Your Control

Deploy within your cloud environment or use our managed service

Implement your data governance policies & access controls

Maintain your security standards & compliance requirements

Control data residency & retention policies


Your Standards, Your Control

Deploy within your cloud environment or use our managed service

Implement your data governance policies & access controls

Maintain your security standards & compliance requirements

Control data residency & retention policies


Your Standards, Your Control

Deploy within your cloud environment or use our managed service

Implement your data governance policies & access controls

Maintain your security standards & compliance requirements

Control data residency & retention policies


Development-Friendly

Comprehensive REST APIs & SDK support

Milemarker™ DevTools CLI for rapid deployment & automation

Webhook infrastructure for event-driven architectures

Command-line tools that ship analytics in minutes, not weeks


Development-Friendly

Comprehensive REST APIs & SDK support

Milemarker™ DevTools CLI for rapid deployment & automation

Webhook infrastructure for event-driven architectures

Command-line tools that ship analytics in minutes, not weeks


Development-Friendly

Comprehensive REST APIs & SDK support

Milemarker™ DevTools CLI for rapid deployment & automation

Webhook infrastructure for event-driven architectures

Command-line tools that ship analytics in minutes, not weeks


Development-Friendly

Comprehensive REST APIs & SDK support

Milemarker™ DevTools CLI for rapid deployment & automation

Webhook infrastructure for event-driven architectures

Command-line tools that ship analytics in minutes, not weeks


Operational Excellence

24/7 infrastructure monitoring & alerting

Multi-region redundancy & disaster recovery

Performance analytics & optimization recommendations

Dedicated technical support & success management


Operational Excellence

24/7 infrastructure monitoring & alerting

Multi-region redundancy & disaster recovery

Performance analytics & optimization recommendations

Dedicated technical support & success management


Operational Excellence

24/7 infrastructure monitoring & alerting

Multi-region redundancy & disaster recovery

Performance analytics & optimization recommendations

Dedicated technical support & success management


Operational Excellence

24/7 infrastructure monitoring & alerting

Multi-region redundancy & disaster recovery

Performance analytics & optimization recommendations

Dedicated technical support & success management

Implementation
Implementation
Implementation
That Respects Your Process
That Respects Your Process
That Respects Your Process
Technical Discovery
Work with your team to understand current architecture, security requirements, and integration needs.

Technical Discovery
Work with your team to understand current architecture, security requirements, and integration needs.

Technical Discovery
Work with your team to understand current architecture, security requirements, and integration needs.

Technical Discovery
Work with your team to understand current architecture, security requirements, and integration needs.

Proof of Concept
Sandbox environment to validate technical approach and security compliance before full deployment.

Proof of Concept
Sandbox environment to validate technical approach and security compliance before full deployment.

Proof of Concept
Sandbox environment to validate technical approach and security compliance before full deployment.

Proof of Concept
Sandbox environment to validate technical approach and security compliance before full deployment.

Phased Rollout
Implement core integrations first, then expand based on your team’s capacity and priorities.

Phased Rollout
Implement core integrations first, then expand based on your team’s capacity and priorities.

Phased Rollout
Implement core integrations first, then expand based on your team’s capacity and priorities.

Phased Rollout
Implement core integrations first, then expand based on your team’s capacity and priorities.

Ongoing Partnership
Regular technical reviews, architecture optimization, and roadmap alignment with your long-term strategy.

Ongoing Partnership
Regular technical reviews, architecture optimization, and roadmap alignment with your long-term strategy.

Ongoing Partnership
Regular technical reviews, architecture optimization, and roadmap alignment with your long-term strategy.

Ongoing Partnership
Regular technical reviews, architecture optimization, and roadmap alignment with your long-term strategy.





Why CTOs
Why CTOs
Why CTOs
Trust Milemarker™
Trust Milemarker™
Trust Milemarker™


Enterprise Security
SOC 2 Type II compliance, penetration testing, and security practices that meet institutional standards.


Enterprise Security
SOC 2 Type II compliance, penetration testing, and security practices that meet institutional standards.


Enterprise Security
SOC 2 Type II compliance, penetration testing, and security practices that meet institutional standards.


Enterprise Security
SOC 2 Type II compliance, penetration testing, and security practices that meet institutional standards.


Architectural Flexibility
Works with your existing infrastructure decisions, doesn’t force you to rebuild everything.


Architectural Flexibility
Works with your existing infrastructure decisions, doesn’t force you to rebuild everything.


Architectural Flexibility
Works with your existing infrastructure decisions, doesn’t force you to rebuild everything.


Architectural Flexibility
Works with your existing infrastructure decisions, doesn’t force you to rebuild everything.


Vendor Independence
Open architecture that prevents vendor lock-in and supports your technology evolution.


Vendor Independence
Open architecture that prevents vendor lock-in and supports your technology evolution.


Vendor Independence
Open architecture that prevents vendor lock-in and supports your technology evolution.


Vendor Independence
Open architecture that prevents vendor lock-in and supports your technology evolution.


Technical Partnership
We work with your team as technology partners, not just another vendor to manage.


Technical Partnership
We work with your team as technology partners, not just another vendor to manage.


Technical Partnership
We work with your team as technology partners, not just another vendor to manage.


Technical Partnership
We work with your team as technology partners, not just another vendor to manage.
The Bottom Line
The Bottom Line
The Bottom Line
You don't need to choose between business requirements & technical standards.
You don't need to choose between business requirements & technical standards.
You don't need to choose between business requirements & technical standards.

Milemarker™ gives you both:
Milemarker™ gives you both:
Milemarker™ gives you both:

Enterprise data infrastructure that scales

Security & compliance that meets your standards

Integration capabilities that satisfy business demands

Technical control that respects your architecture

Ready to See the Architecture?
Deep-dive into architecture, security, and integration capabilities.

Ready to See the Architecture?
Deep-dive into architecture, security, and integration capabilities.

Ready to See the Architecture?
Deep-dive into architecture, security, and integration capabilities.

Ready to See the Architecture?
Deep-dive into architecture, security, and integration capabilities.

Phone
+1 (470) 502-5600
Mailing Address
Milemarker
PO Box 262
Isle Of Palms, SC 29451-9998
Legal Address
Milemarker Inc.
16192 Coastal Highway
Lewes, Delaware 19958
Built by Teams In:
Atlanta, Charleston, Cincinnati, Denver, Los Angeles, Omaha & Portland.
Partners




Platform
Solutions
© 2026 Milemarker Inc. All rights reserved
DISCLAIMER: All product names, logos, and brands are property of their respective owners in the U.S. and other countries, and are used for identification purposes only. Use of these names, logos, and brands does not imply affiliation or endorsement.

Phone
+1 (470) 502-5600
Mailing Address
Milemarker
PO Box 262
Isle Of Palms, SC 29451-9998
Legal Address
Milemarker Inc.
16192 Coastal Highway
Lewes, Delaware 19958
Built by Teams In:
Atlanta, Charleston, Cincinnati, Denver, Los Angeles, Omaha & Portland.
Partners




Platform
Solutions
© 2026 Milemarker Inc. All rights reserved
DISCLAIMER: All product names, logos, and brands are property of their respective owners in the U.S. and other countries, and are used for identification purposes only. Use of these names, logos, and brands does not imply affiliation or endorsement.

Phone
+1 (470) 502-5600
Mailing Address
Milemarker
PO Box 262
Isle Of Palms, SC 29451-9998
Legal Address
Milemarker Inc.
16192 Coastal Highway
Lewes, Delaware 19958
Built by Teams In:
Atlanta, Charleston, Cincinnati, Denver, Los Angeles, Omaha & Portland.
Partners




Platform
Solutions
© 2026 Milemarker Inc. All rights reserved
DISCLAIMER: All product names, logos, and brands are property of their respective owners in the U.S. and other countries, and are used for identification purposes only. Use of these names, logos, and brands does not imply affiliation or endorsement.

Phone
+1 (470) 502-5600
Mailing Address
Milemarker
PO Box 262
Isle Of Palms, SC 29451-9998
Legal Address
Milemarker Inc.
16192 Coastal Highway
Lewes, Delaware 19958
Built by Teams In:
Atlanta, Charleston, Cincinnati, Denver, Los Angeles, Omaha & Portland.
Partners







